AWS Solutions Architect: Exam Question Deep Dive #2
Deep dive into a question from the AWS Solutions Architecture Professional Exam about cost control options using AWS Organizations, IAM, CloudWatch, and AWS Cost Explorer.

AWS Solutions Architect Series
Amazon recently posted a new set of AWS exam questions for the Solutions Architect Professional (SAP-C01) exam, and I am excited to dig into them. As I have prepared this and other AWS exams, I found dissecting exam questions helpful to grow my AWS knowledge. This post is a bite-sized study guide that will hopefully expand your knowledge of AWS and help you on your journey to becoming a Solutions Architect as well.
For each post in this series, I will choose one AWS Solutions Architect Professional exam question. We will explore the required knowledge and strategy to find the right answer and learn about a few AWS services along the way. This question requires knowledge about AWS Organizations, IAM, CloudWatch, and AWS Cost Explorer.
The following question is from the Solutions Architect, Professional (SAP-C01) — Sample Exam Questions provided by Amazon.
An enterprise has a large number of AWS accounts owned by separate business groups. One of the accounts was recently compromised. The attacker launched a large number of instances, resulting in a high bill for that account.
The security breach was addressed, but management has asked a solutions architect to develop a solution to prevent excessive spending in all accounts. Each business group wants to retain full control over its AWS account.
Which solution should the solutions architect recommend to meet these requirements?
-
A) Use AWS Organizations to add each AWS account to the master account. Create a service control policy (SCP) that uses the
ec2:instanceTypecondition key to prevent the launch of high-cost instance types in each account. -
B) Attach a new customer-managed IAM policy to an IAM group in each account that uses the
ec2:instanceTypecondition key to prevent the launch of high-cost instance types. Place all of the existing IAM users in each group. -
C) Enable billing alerts on each AWS account. Create Amazon CloudWatch alarms that send an Amazon SNS notification to the account administrator whenever their account exceeds the spending budget.
-
D) Enable AWS Cost Explorer in each account. Regularly review the Cost Explorer reports for each account to ensure spending does not exceed the planned budget.
First, let’s make sure we understand the question. Management is looking for a way to prevent excessive spending in all accounts, while each group retains full control of their account. These two items are vital in differentiating the answers. We should ask ourselves to what degree each answer satisfies these two requirements. We also want to assess each possible answer against the AWS well-architected framework.
Answer A
To see if this could be the right answer, we need to know about how service control policies (SCPs) work in AWS Organizations. AWS Organizations is a service that allows large companies to centralize billing, security, and compliance policies across multiple AWS accounts. A single root account is a parent to multiple Organizational Units (OUs). The company’s root account administrator creates OUs and associates the individual AWS accounts with the OUs. AWS Organizations can create new AWS accounts or invite pre-existing accounts to join the organization.
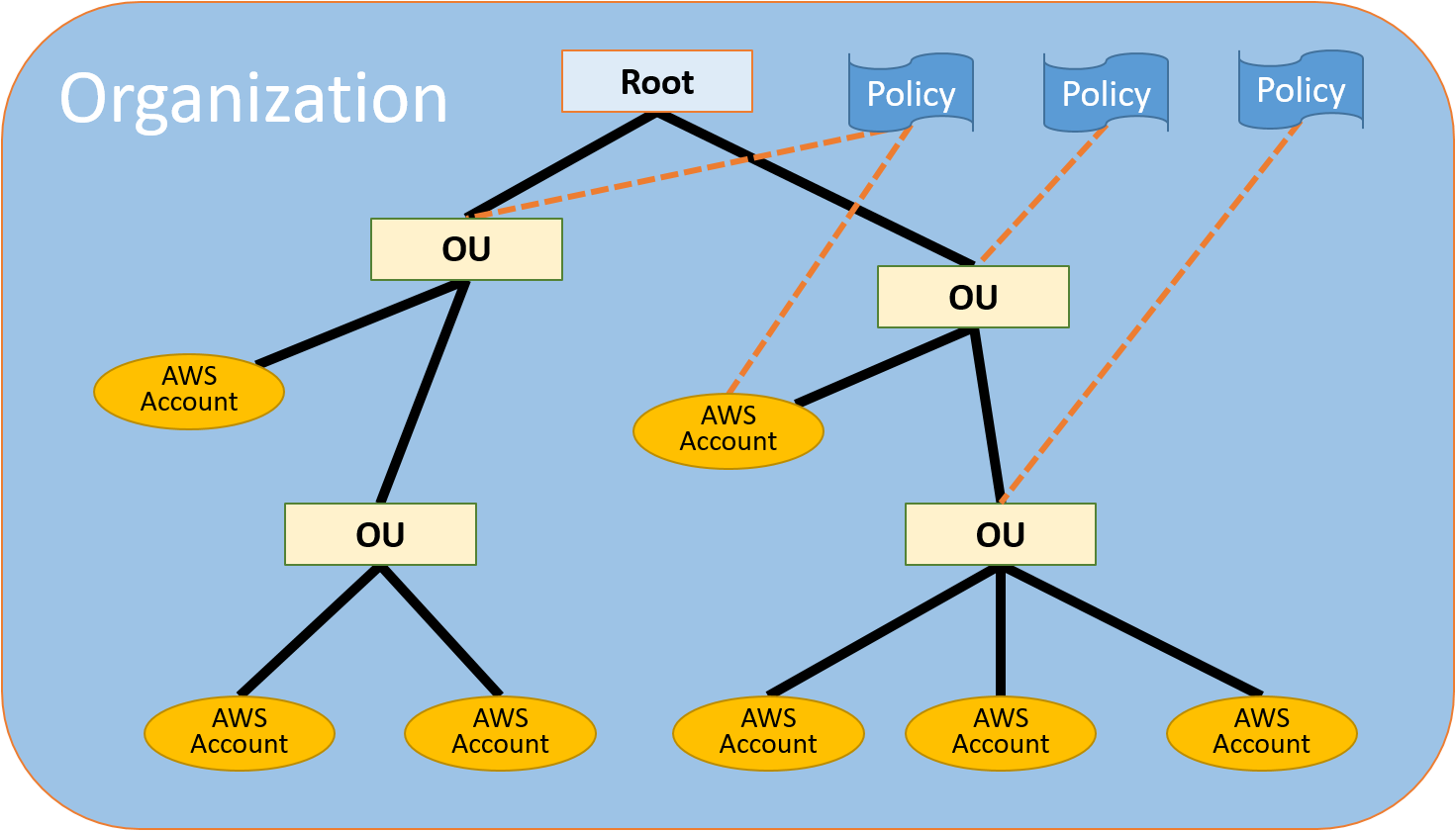
The root account defines SCPs and attaches them to Organizational Units (OUs). These SCPs restrict how and what services can be used by the AWS accounts under that OU. OUs can implement their own SCPs, but can only allow services that are also allowed by the policies attached to it by the root account.
SCPs are text files that follow the same format as IAM permission policies. For example, the following SCP only allows t2.micro instances.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "RequireMicroInstanceType",
"Effect": "Deny",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"StringNotEquals":{
"ec2:InstanceType":"t2.micro"
}
}
}
]
}
- How well does this solution prevent excessive costs? Rating: poor. While you can prevent expensive instance types, nothing stops someone from spinning up lots of cheaper instances, therefore not controlling overall costs. It also only addresses EC2 and does not account for any other services that the bad guys could use and rack up charges.
- How well does this solution allow groups to retain full control of their accounts? Rating: poor. The root account can restrict the services used by each OU, therefore taking away some of their control.
Answer B
This answer is very similar to the last one. In this case, however, we are allowing each group to create their own IAM policy restricting certain EC2 instance types, not implementing policy from above. Remember, SCPs have the same format as IAM policies; therefore, these policies will be very similar to the SCP shown in answer A.
- How well does this solution prevent excessive costs? Rating: poor. For the same reasons as answer A, this is not a good solution for preventing excessive costs.
- How well does this solution allow groups to retain full control of their accounts? Rating: good. This solution gives control to the individual AWS account administrators, even if the direction to restrict EC2 instance type usage comes from the top.
Answer C
This answer uses the CloudWatch service to monitor metrics, like estimated billing, and allows users to set alerts and alarms when certain thresholds are met. Some usefule CloudWatch terminology:
- Metrics - values measured by CloudWatch. These can be things like CPU usage on EC2, disk reads and writes, and estimated monthly billing.
- Alarms - Configured to watch metrics for specific conditions or values.
- Alerts - Notifications sent to users when alarms go off. Notifications are sent using the Simple Notification Service (SMS), which can send emails and SMS messages.
You can monitor many things in your AWS infrastructure using CloudWatch. When metrics register a specific condition or value, CloudWatch can send notifications, start or stop EC2 instances, and other actions. This sounds like a useful tool to use for this problem.
- How well does this solution prevent excessive costs? Rating: good. This solution provides the best alternative to actually preventing excessive costs. Users can set CloudWatch alarms to different thresholds like 80%, 95%, and 100% of a certain budget. This would alert account managers to any potential overages before they occur and allow them to take appropriate action to reduce costs.
- How well does this solution allow groups to retain full control of their accounts? Rating: good. This solution distributes control to the individual AWS account administrators. Each account may have different monthly budgets, and CloudWatch allows them to manage these different costs within the group.
Answer D
This answer uses AWS Cost Explorer to review costs regularly. AWS Cost Explorer is a service that, big surprise, allows users to “explore” the costs they are racking up in their account and how to save money. The two main features of Cost explorer are Savings Plans and Reserved Instance Management. Savings Plans were introduced in November 2019 as a new flexible pricing model that may replace reserved instances at some point in the future. Savings Plans allow you to get discounted prices on EC2 instances by committing to a term (usually 1 or 3 years).
- How well does this solution prevent excessive costs? Rating: poor. Cost Explorer will help you minimize costs for resources you already know you are planning to use. If one of the groups in this organization was planning on running 150 c3.xlarge instances non-stop for a year, Cost Explorer could help save 60-70%on their bill. It does nothing for unexpected resource use and, therefore, will not help control the excessive costs described in this question.
- How well does this solution allow groups to retain full control of their accounts? Rating: good. Cost Explorer can be used for an individual AWS account and within AWS Organizations. Using it does not necessarily prevent the individual groups from retaining control, although the root account can restrict permissions to the linked accounts that are part of the AWS Organization.
C is the correct answer. This option well supports both requirements (cost prevention & full control for each group). All others fail to support one or both of these needs.
Thanks for reading! Please leave feedback and let me know if you enjoyed this post. If you are interested in other posts, I have written about other AWS services, cloud solutions, and architectures, check me out on Medium. https://medium.com/@ezrabowman
